How tech companies can help clients prevent ransomware attacks (and weather a lawsuit if they sue)

There’s no questioning the harm cybercrimes like ransomware can inflict on a client. But what about the risks your own business could face if your client becomes a ransomware victim?
If a client is successfully attacked, it could damage your reputation and your bottom line. And worse: you could easily find yourself at the wrong end of a lawsuit.
No matter your clients’ size or industry, they could be in danger of a ransomware attack. And your smaller clients are especially vulnerable as they have less protection for their devices and networks.
Fortunately, providing the right guidance can reduce your risk and theirs. Read on to learn ways to safeguard and educate clients on ransomware prevention – and how to protect your tech company if a client attack happens.
What do I need to teach my clients about the types of ransomware attacks?
Your client might not realize the ransom is merely part of the overall price of an attack. The inability to access mission-critical data for even a short time may cost more in the long run.
And if a business chooses not to pay, or pays but never receives the promised encryption key, the long-term costs can be devastating.
Cybercriminals are constantly inventing new ways to profit from hacking into businesses. Take the time to educate your clients on the five basic types of ransomware attacks:
Cryptoware
Also known as encrypting ransomware, cryptoware is the most common type of ransomware. It prevents access to files by encrypting data and requires a ransom payment to restore it.
Lockerware
Lockerware (or non-encrypting ransomware) blocks access to systems and files but doesn’t encrypt the data. It typically locks a computer or device until a ransom is paid.
Mobile device ransomware
Mobile device ransomware blocks access to smartphones by planting malware through fake applications, infected websites, or operating system security holes. A ransom must be paid to unlock the device or restore data.
Leakware
With leakware (aka “extortionware”), cybercriminals threaten to make sensitive data public unless a ransom is paid. It’s the opposite of traditional ransomware: instead of locking you out of your data, it releases it to the world.
Master boot record (MBR) ransomware
This ransomware encrypts a hard drive’s master boot record, preventing the operating system from even booting up. A ransom must be paid to decrypt the MBR.
No matter the type of ransomware attack, they all begin the same way. The first step in an attack is trying to gain access to your client’s systems. Your job is to keep them out.
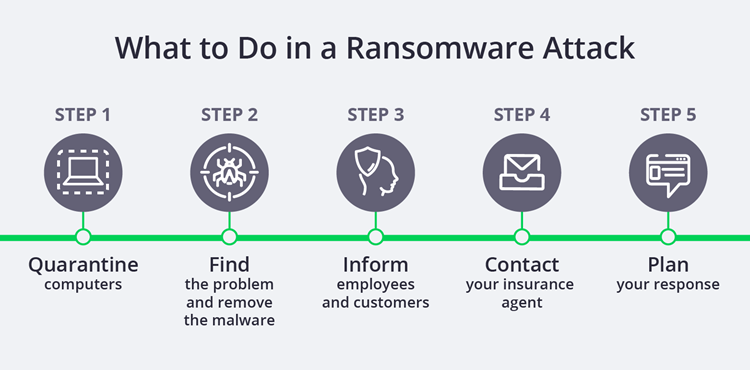
How to reduce a client’s risk of a ransomware attack
When considering the risk of an attack on your client’s business, think in terms of “when,” not “if.”
You may not be able to stop cybercriminals from launching an attack, but you can lower the odds that they’ll succeed.
Learn your clients’ potential security weaknesses early in the sales process, even if you don’t offer a formal risk analysis. Your clients probably have limited IT dollars to spend, and some cybersecurity options can be pricey.
This feedback will help you create a security bundle of software and services that’s on point and within budget. And you can take steps to help prevent a successful ransomware attack against your client:
Educate and train clients
You know how quickly ransomware can spread across a network. Clients often don’t. That’s why educating them on IT best practices and common risks is the first place to start.
You may want to conduct training on how attackers use social engineering tactics like phishing to access networks. Explain the dangers of:
- visiting unfamiliar websites
- opening email from unknown senders
- downloading unexpected files
- clicking on suspicious links
- using weak passwords
Regular reminders of best practices coupled with strong spam filters and anti-virus software can go a long way. Be sure to train your client’s new employees and contractors, and tailor your training for less technical staff.
Maintain a strong firewall
A firewall is arguably the most critical cybersecurity tool you have. But to be effective, your firewall must be properly managed and maintained.
Always double and triple check your work when you change configurations.
Install client-side anti-virus, encryption, and email filtering software
If a firewall is the moat that keeps hackers out, then encryption, anti-virus software, and spam filters are the guard dogs that patrol it.
Whichever software you recommend, ensure clients install and regularly update it to detect and remove malware from their network. (This can be a nice add-on service for your business.)
You can also create email filters to isolate messages that may contain malware or suspect links. Your clients probably don’t have the expertise or time (or both) to set this up.

Stress the importance of a VPN
More and more companies rely on remote work to run their business. If your clients conduct work remotely, always use a trusted VPN.
You may also want to encourage them to avoid using Microsoft Remote Desktop Protocol (RDP) as it’s a common target in ransomware attacks. If they do use it, be sure it’s used along with a VPN.
Stay up-to-date and secure your network
It’s vital that you keep current on your clients’ operating system’s security patches – as well as your own. Hackers will often take advantage of vulnerabilities to gain access to a network.
You can secure any interfaces by enabling multi-factor authentication and limiting access to the network. Remote or administrative interfaces with your primary network environment can leave you susceptible to a ransomware attack.
Put them on a data backup plan
The best way to minimize damage recovery time if an attack occurs is with frequent data backups. How much data your client has and how sensitive it is will help determine how you backup your data, but backup and redundancy options boil down to:
- network attached storage
- cloud storage
- RAID
The best backup is one that’s completely separate from your primary network environment.
You and your clients should regularly test your backup programs and make redundant copies of your data. These steps are critical for an effective business continuity plan.
If cloud storage raises security concerns with clients, bring up encryption options that prevent data access if the cloud service provider exposes data.
Of course, encryption comes with disadvantages. Be direct with your client about the risks of data recovery compared to unencrypted files.
They may decide to encrypt only a portion of their files, such as their most sensitive data.
Stay vigilant
Always be on the lookout for possible signs of an attack. For example, phishing attempts are often an early warning that a cybercriminal is targeting you or your client.

How to protect your client (and your business) if a ransomware attack succeeds
Despite your best efforts, your client may still experience a ransomware attack. Cybercriminals are constantly evolving their methods and their malware to get past your defenses.
If a ransomware attack does occur, it will likely bring their business operations to a grinding halt. And the costs can be steep if they choose to pay the ransom.
Plus there’s no guarantee that you’ll be able to restore access to their data. Tying to recover data and rebound from an attack can be a long and expensive process.
As a tech company, there’s far more than your reputation at stake. Your client may hold you responsible.
To protect your business from ransomware-related lawsuits, consider insurance policies to help cover your losses.
Technology errors and omissions insurance
Technology errors and omissions insurance (also called tech E&O) can protect your business from client lawsuits claiming your mistakes, oversights, or negligence caused them harm.
Tech E&O includes third-party cyber liability coverage for the legal costs of a data breach, ransomware attack, or other cybercrime. Covered costs include:
- lawyers’ fees
- settlements
- judgments
- other legal costs
These policies are a good idea for any tech business. But they’re especially valuable if you have large client risk or could face client accusations of failing to prevent a cybercrime.
As a tech company, there’s far more than your reputation at stake. Your client may hold you responsible.
Cyber liability insurance
While tech E&O covers the legal costs of a client lawsuit, you’ll need cyber insurance to protect you if your business is attacked.
The main difference between tech E&O and a cyber liability policy is straightforward:
- Tech errors and omissions protects you from harm to a third party, like a client.
- Cyber liability protects you from direct harm to your business.
A cyber liability policy provides first-party cyber liability coverage. This insurance covers your business costs for:
- ransomware demands
- hiring experts to assist with negotiations
- investigating an attack
- notifying customers
Shielding yourself and your clients from ransomware attacks is serious business. Preventing an attack is your best line of defense. But you also need to be prepared for the aftermath of an attack.
The right insurance coverage can help keep your tech business safe from lawsuits and other risks to ensure your continued success.
Complete Insureon’s easy online application today to compare quotes for business insurance from top-rated U.S. carriers. Once you find the right policy for your small business, you can begin coverage in less than 24 hours.







